Brivan Cyber
We have an expert team of cybersecurity specialists dedicated to safeguarding your digital world. Our team comprises of highly skilled professionals who have acquired industry-leading certifications and qualifications. Our partnership with leading global service providers enables us to offer best-in-class cybersecurity services to our customers. Protect your digital environment with Brivan Cyber
End-To-End services in all aspects of cybersecurity
A one stop solution for your protection.
Identify
What processes and assets need protection?
Protect
Implement appropriate safeguards to ensure the protection of assets of enterprises
Detect
Implement appropriate mechanisms to identify the occurence of cybersecurity incidents
Respond
Develop techniques to contain the impact of cybersecurity events
Recover
Implement the appropriate processes to restore capabilities and services impaired due to cybersecurity events
We bring you the world's best in cybersecurity
In partnership with the industry’s highest rated services providers
We believe in collaboration and understand the power of partnerships in delivering superior cybersecurity solutions. To enhance our offerings, we have forged strategic alliances with leading technology providers and industry experts. These partnerships enable us to access cutting-edge tools, resources, and best practices, allowing us to deliver the most suitable solutions for your organization.
Risk Assessment
For compliance and security readiness
Identify Assets
• Tangible and Intangible
• People
• Process
• Technology
Identify Threats & Vulnerabilities
• Environment
• Human
• Social
• Internal & External
Assess Current State
• Are we doing the right things?
• Are we doing them the right way?
• Are we getting them done well?
• Are we getting the benefits?
Evaluate Risks
• Business Impact Analysis
• Quantiative & Qualitative Analysis
• Probability and Impact Assessment
• Risk Prioritization
Assign Ownership
• An Individual not a team or department
Vulnerability Assessment & Penetration Testing (VAPT)
Verifying and assessing your security posture
Information Congregation
Gather information about the target system
Vulnerability Assessment
Reporting/Result Analysis
Threat Analysis
Define Scope and create threat profile
Exploitation/In-depth penetration testing
Security information & Event management (SIEM)
Auditing and analyzing your event logs
Log Collection
Log Analysis
Event Correlation
Log Forensics
IT Compliance
App Log Monitoring
Object Access Auditing
SIEM
SIEM software products and services are used to combine data on security information management and security events.
Real-Time
User Activity Monitoring
Dashboards
Reporting
File Integrity Monitoring
System & Device Log Monitoring
Log Retention
The Fastest MDR on the Planet
Rely on machine-speed technology run by dedicated analysts to adapt to today’s threat landscape.
Follow-the-Sun Coverage
Our analysts monitor 24x7x365 for changes to your environment, and are prepared to respond no matter where you are in the world.
Shorter MTTD & MTTR
SentinelOne’s 18-minute MTTR makes Vigilance the fastest MDR service in the business.
SOC Team Augmentation
Offloading day-to-day operationalization and threat hunting to our MDR experts lets your team refocus on program strategy.
Fewer Alerts, More Context
Vigilance adds human context to Storyline™ technology, saving even more time spent aggregating, correlating, and contextualizing alerts.
A Human Lens to Security
As extensions of your team, our analysts learn to triage and prioritize events based on the unique needs of your program.
Documentation & Reporting
Every identified threat in your environment is reviewed, documented, and incorporated as part of your ongoing reporting cadence.
Security Operations Center
Key components of SOC
1. Key SOC Personnel
- Soc Manager
- Soc Analyst
- Soc Engineer
- Soc Operator
2. Critical managed SOC Process
- Vulnerability discovery process
- Vulnerability remediation and tracking
- Incident analysis, triage, and reporting
- Incident closure, and post-incident activities
3. Vital SOC Technologies
- SIEM
- IDS / IPS
- EDR / XDR
- Cyber Threat Intelligence
Virtual Chief Information Security Officer
(vCISO)
Business Experience
A leader who has the business acumen to talk to and speak with senior leaders and board members.
Cyber Threats and Security
Understanding of threat motives, actors techniques and their compensating controls.
Risk
Takes a business approach to security has direct experience to appreciate uniqueness and challenges to industry.

Information Systems
Expertise with networking, servers and workstations, applications and other systems.
People Skills
Approachable communicator, understands business acumen translator.
Compliance
Strong familiarity with regulations experience working with internal and external auditors.
World-Class training modules
Measurable enterprise-strength pre & post training
Train your users
The world's largest library of security awareness training content. Automated training campaigns with scheduled reminder emails.
Phish your users
Best-in-class, fully automated simulated phishing attacks, thousands of templates with unlimited usage, and community phishing templates.
See the results
Enterprise-strength reporting, showing stats and graphs for both training and phishing, ready for management. Show the great ROI!
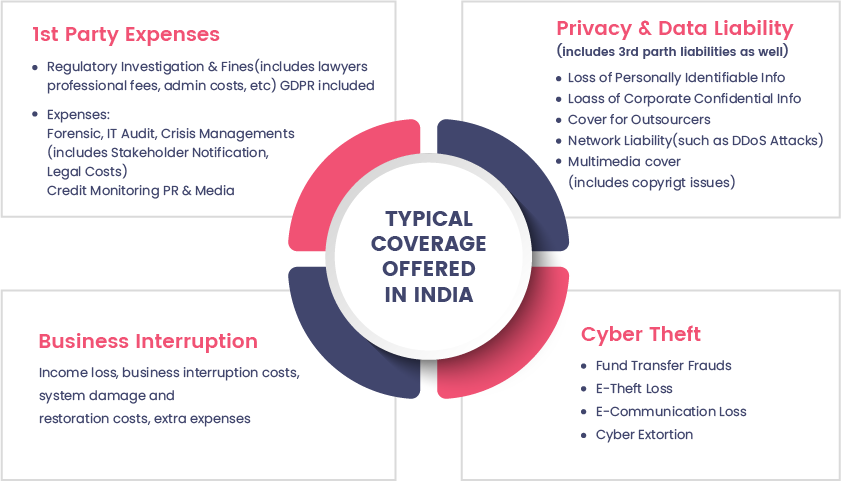
Cyber-Insurance Readiness
And insurance assessment support
Global Cyber Insurance Market
Opportunities and forecast, 2019-2026
Cyber Insurance Market is expected to garner $28.6 Billion by 2026.
Growing at a CAGR of 24.9% (2019-2026)
Why are we your best cybersecurity partner?
Comprehensive Solutions
Vast portfolio of 10+ security services
24x7 Monitoring
Along with real-time alerting & responses
Integrated & Automated
Next-gen AI-led which integrates with customer-side tools
Simplified Pricing
Attractive pricing options leading to lower operations cost
